I’m excited to announce the release of SPCHR. Pronounced as “speaker”. I know, I know. My apologies, it was too late at night and that’s the best I could come up with 😉
- It is a Windows desktop application for speech-to-text transcription.
- You can use it to “add” voice input to applications that don’t natively support it. It works anywhere you can type or paste text.
- You can use it entirely locally on your PC if you like, so it is private and secure.
Key Features
- Flexible: SPCHR can use either Azure Speech Services or a local OpenAI Whisper model, giving you the flexibility to choose between cloud-based and local transcription.
- Zero Configuration: The application works immediately with local Whisper processing – no account setup required!
- Global Hotkey: Start and stop recording from any application with Ctrl+Alt+L.
- Seamless Integration: Transcribed text is automatically pasted into your active window.
Getting Started
- Clone the repository
- Build the solution using Visual Studio and run it
- Press Ctrl+Alt+L and start speaking
- Watch as your words appear in your active window
- For those wanting cloud-based transcription, simply add your Azure Speech Services credentials to the configuration file.
Open Source
SPCHR is released under the MIT License, and I welcome contributions from the community. Whether you’re interested in adding features, fixing bugs, or improving documentation, your help is appreciated.
Check out GitHub repository
What’s next
This is just the beginning for SPCHR. Several improvements can be done:
- Additional language support
- Customizable hotkeys
- Installer
- UI Enhancements
- AI Enhanced Features
Try it out
Ready to transform how you interact with your computer? Visit the GitHub repository to get started with SPCHR today.
I’m excited to see how you’ll use SPCHR in your workflow and look forward to your feedback!

![Run
Time range : Last 24 hours
E] Save v
14 Share v
1
2
3
4
5
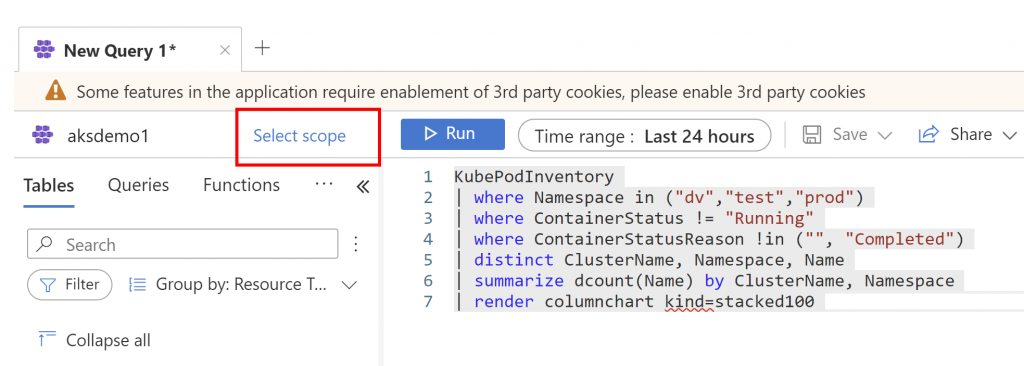
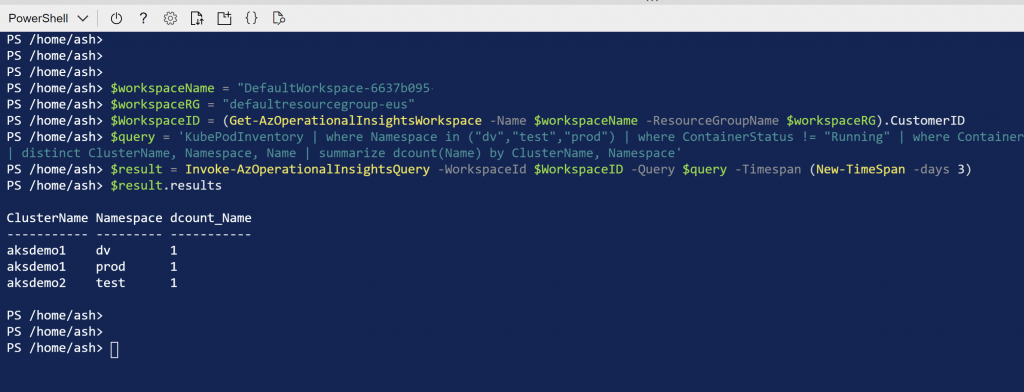
KubePodInventory
I where Namespaceän ('dv', 'test', 'prod')
I where ContainerStatusu !=
"Running"
I where ContainerStatusReasone ! in ('I", "Completed")
I distinct Namespace, Name
Results Chart
@ Display time (UTC+OO:OO) v
Columns v
Completed. Showing results from the last 24 hours.
>
Namespace
dv
prod
Y Name Y
app2
app2](https://www.tewari.info/wp-content/image-7.png)
![Run
Time range : Last 24 hours
E] Save v
14 Share v
+ New alert rule
Export v
Pin to dashboard
1
2
3
4
5
6
7
8
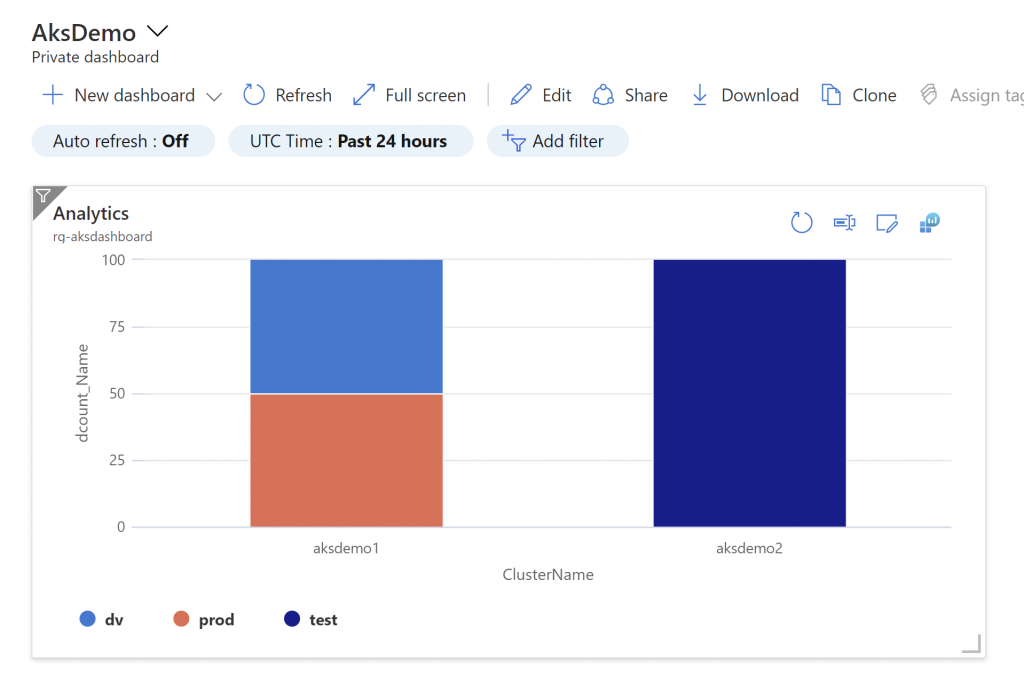
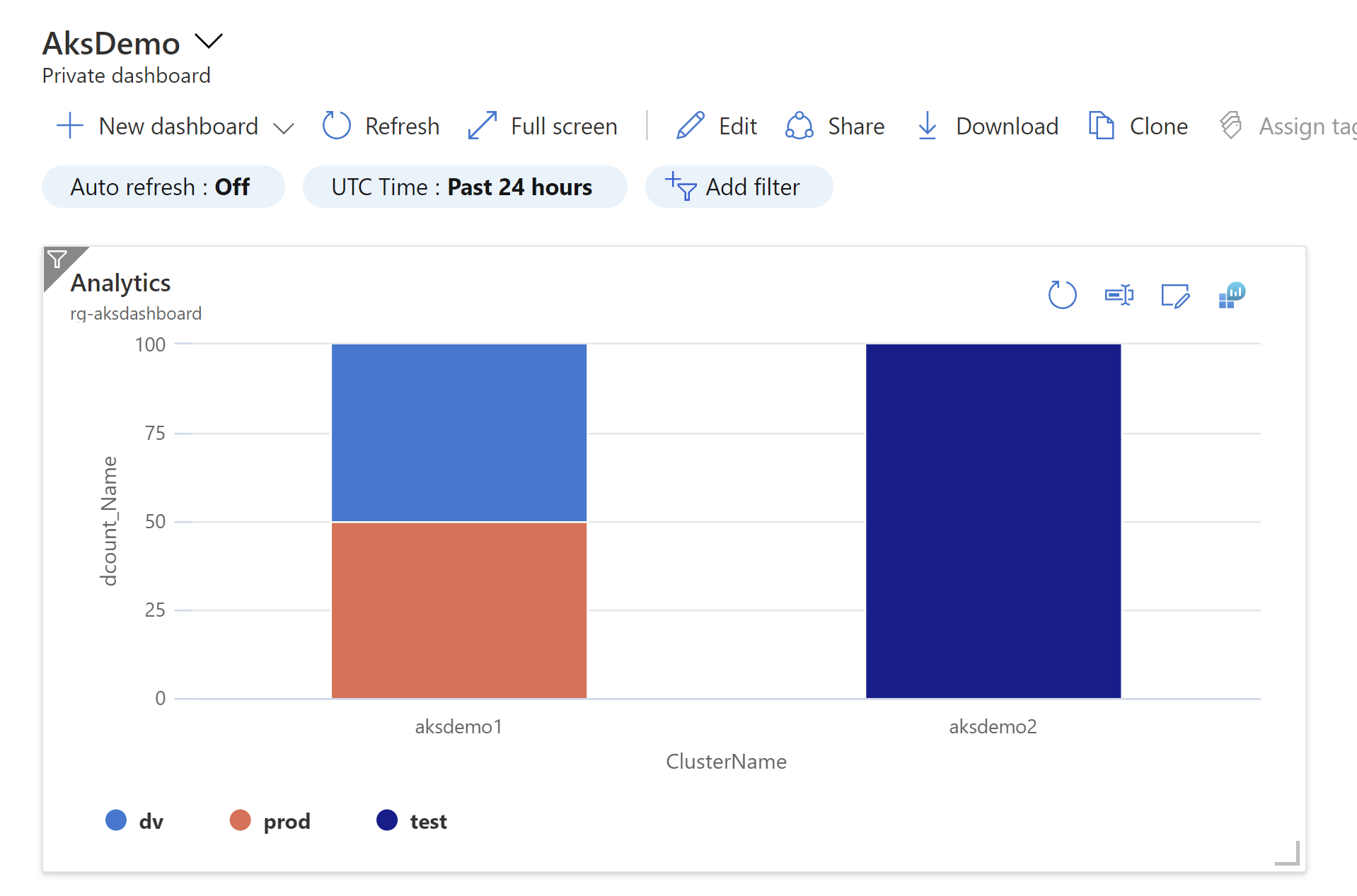
KubePodInventory
I where Namespace in ('dv', 'test', 'prod')
I where ContainerStatus ! =
"Running"
I where ContainerStatusReason ! in ('I", "Completed")
I distinct ClusterName, Namespace, Name
summarize dcount(Name) by ClusterName, Namespace
render columnchart kind=stacked100
Results
Chart
@ Display time (UTC+OO:OO) v
Completed. Showing results from the last 24 hours.
00:00.7
2 records
z
o
100
50
dv
O
aksdemol
ClusterName
prod
Activate Windows
Go to Settings to activate Windows.](https://www.tewari.info/wp-content/image-8-1024x582.png)